WireGuard VPN solution
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache.
Ocata integrates the WireGuard VPN solution using open-source technologies such as ‘Ubuntu Linux’, ‘WireGuard’, ‘docker’, and ‘wg-easy’, allowing you to set up your own VPN server on Amazon AWS in just 5 minutes.
Features
- All-in-one: WireGuard + Web UI.
- Easy installation, simple to use.
- List, create, edit, delete, enable & disable clients.
- Show a client’s QR code.
- Download a client’s configuration file.
- Statistics for which clients are connected.
- Tx/Rx charts for each connected client.
- Gravatar support.
Usage Instructions
After subscribing on AWS Marketplace, an EC2 instance customized for wireguard will be automatically created, you can launch it by using the 1-Click Launch view in AWS Marketplace.
Launching on Amazon EC2 using 1-Click launch
To launch on Amazon EC2 using 1-Click launch
- On the Launch this software page, choose Launch from website in the Choose Action dropdown, and review the default settings. If you want to change any of them, do the following:
In the EC2 Instance Type dropdown list, choose an instance type.
In the VPC Settings and Subnet Settings dropdown lists, select the network settings you want to use.
In the Security Group Settings, choose an existing security group, or choose Create New Based On Seller Settings to accept the default settings. For more information about security groups, see Amazon EC2 security groups for Linux instances in the Amazon EC2 User Guide for Linux Instances.
Expand Key Pair, and choose an existing key pair if you have one. If you don’t have a key pair, you’re prompted to create one. For more information about Amazon EC2 key pairs, see Amazon EC2 key pairs.
- When you’re satisfied with your settings, choose Launch.
Your new instance is launched with the WireGuard VPN solution customized by Ocata running on it. From here, you can view the instance details, create another instance, or view all instances of your software.
Before connecting to the WireGuard service, please complete the following prerequisites.
1. Associate an Elastic IP address
As with any server, you want to assign it an Elastic IP address, which is like a static IP address. Otherwise, your public IP address will change whenever you stop the EC2 instance.
- Go to the AWS console > EC2 > Elastic IPs
- Click Allocate new address
- Click Allocate
- Click on the newly allocated IP address
- Under Actions, select Associate address
- From the Instance drop-down, select your EC2 instance
- Click Associate
2. To connect to your EC2 instance
Connect to your instance using the following command:
ssh -i key-pair-name.pem ubuntu@YOUR_SERVER_IP
Replace key-pair-name.pem with the path to your private key file (.pem), and YOUR_SERVER_IP with the Elastic IP address of your server.
For more information about how to connect to your instance, see Connect to your Linux instance using SSH
3. Run WireGuard Easy
To automatically install & run wg-easy, simply run:
$ sudo docker run -d \
--name=wg-easy \
-e WG_HOST=YOUR_SERVER_IP \
-e PASSWORD=YOUR_ADMIN_PASSWORD \
-e WG_DEFAULT_DNS=8.8.8.8,8.8.4.4 \
-v ~/.wg-easy:/etc/wireguard \
-p 51820:51820/udp \
-p 51821:51821/tcp \
--cap-add=NET_ADMIN \
--cap-add=SYS_MODULE \
--sysctl="net.ipv4.conf.all.src_valid_mark=1" \
--sysctl="net.ipv4.ip_forward=1" \
--restart unless-stopped \
weejewel/wg-easy
Replace YOUR_SERVER_IP with your YOUR_SERVER_IP.
Replace YOUR_ADMIN_PASSWORD with a password to log in on the Web UI.
Your configuration files will be saved in
~/.wg-easy
The Web UI will now be available on http://YOUR_SERVER_IP:51821.
4. Use a web browser to access the WebUI at:
http://YOUR_SERVER_IP:51821/
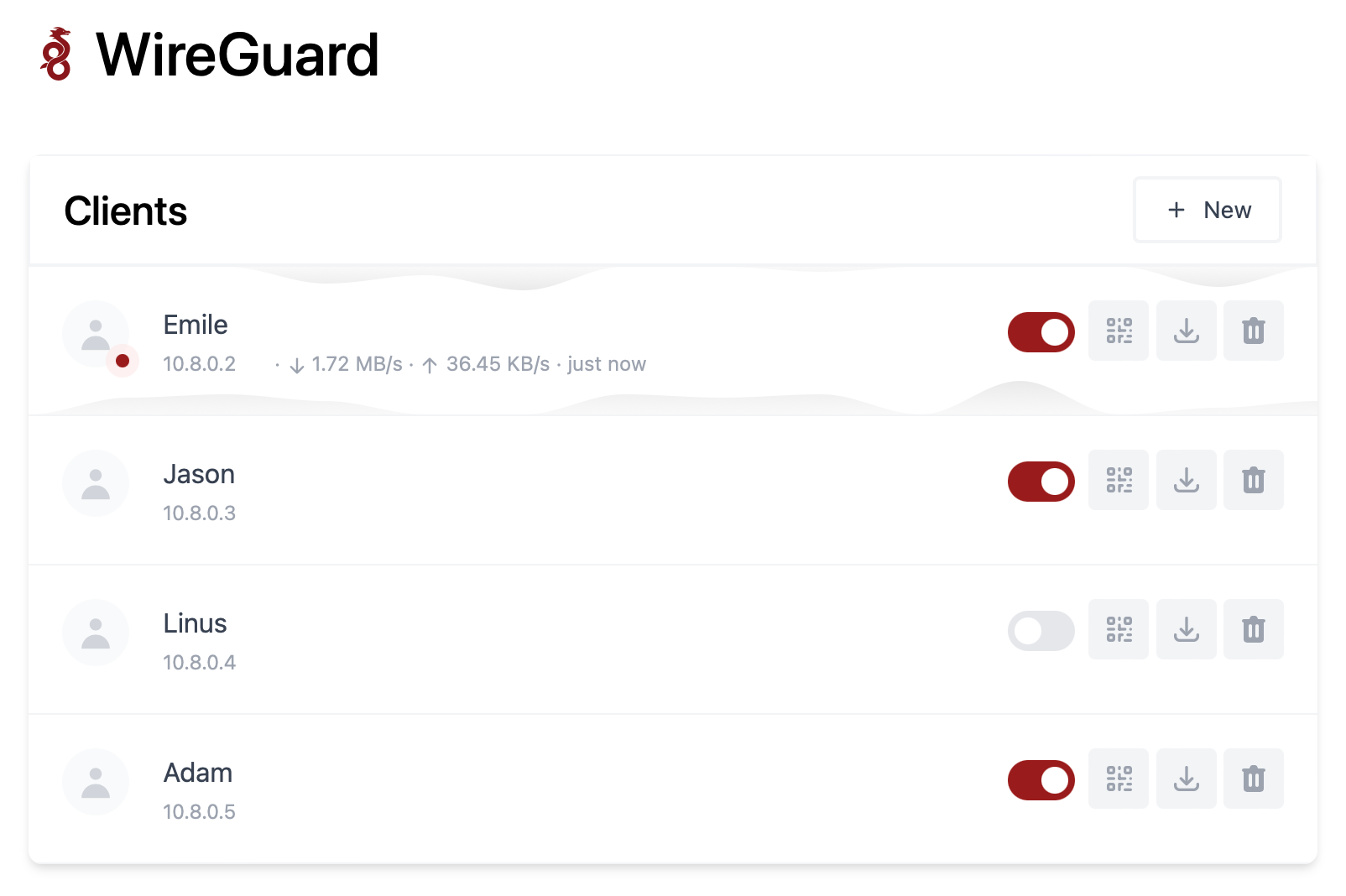
5. Add the user and add the configuration to the client through a QR code.
After linking the VPN server on the client, you will see the user’s connection status in the WebUI.
Congratulations, you’re all set!
Options
These options can be configured by setting environment variables using -e KEY="VALUE" in the docker run command.
| Env | Default | Example | Description |
|---|---|---|---|
PASSWORD | - | foobar123 | When set, requires a password when logging in to the Web UI. |
WG_HOST | - | vpn.myserver.com | The public hostname of your VPN server. |
WG_PORT | 51820 | 12345 | The public UDP port of your VPN server. WireGuard will always listen on 51820 inside the Docker container. |
WG_MTU | null | 1420 | The MTU the clients will use. Server uses default WG MTU. |
WG_PERSISTENT_KEEPALIVE | 0 | 25 | Value in seconds to keep the “connection” open. If this value is 0, then connections won’t be kept alive. |
WG_DEFAULT_ADDRESS | 10.8.0.x | 10.6.0.x | Clients IP address range. |
WG_DEFAULT_DNS | 1.1.1.1 | 8.8.8.8, 8.8.4.4 | DNS server clients will use. |
WG_ALLOWED_IPS | 0.0.0.0/0, ::/0 | 192.168.15.0/24, 10.0.1.0/24 | Allowed IPs clients will use. |
WG_PRE_UP | ... | - | See config.js for the default value. |
WG_POST_UP | ... | iptables ... | See config.js for the default value. |
WG_PRE_DOWN | ... | - | See config.js for the default value. |
WG_POST_DOWN | ... | iptables ... | See config.js for the default value. |
If you change
WG_PORT, make sure to also change the exposed port.
Monitoring and assessing application functions
To monitor and assess application functions
Navigate to your Amazon EC2 console and verify that you’re in the correct region.
Choose Instances and select your launched instance.
Select the server to display your metadata page and choose the Status checks tab at the bottom of the page to review if your status checks passed or failed.
Upgrade
To update to the latest version, simply run:
docker stop wg-easy
docker rm wg-easy
docker pull weejewel/wg-easy
And then run the docker run -d \ ... command above again.
Additional
WireGuard: https://www.wireguard.com/
WG-Easy WebUI: https://github.com/WeeJeWel/wg-easy
WireGuard is a registered trademark of Jason A. Donenfeld. Ocata is not approved, sponsored, or affiliated with WireGuard or with the community.
Changelog
1.0.0
- Initial Release